Python Generate 256 Bit Key
The above code derives a 256-bit key using the PBKDF2 key derivation algorithm from the password s3cr3t.c0d3. It uses a random password derivation salt (128-bit). This salt should be stored in the output, together with the ciphertext, because without it the decryption key cannot be derived again and the decryption will be impossible. Encryption Key Generator. The all-in-one ultimate online toolbox that generates all kind of keys! Every coder needs All Keys Generator in its favorites! It is provided for free and only supported by ads and donations. 64-bit 128-bit 256-bit 512-bit 1024-bit 2048-bit 4096-bit. For example, AES with a 32-byte key is 256-bit AES. Most algorithms # define restrictions on key sizes. For example, AES has 3 choices: 128-bit, 192-bit, # or 256-bit. In the ChaCha20 algorithm, the key size must always be 256-bits (32-bytes). # Both sides (encryptor and decryptor) must be in possession.
This is an exercise in secure symmetric-key encryption, implemented in purePython (only built-in libraries used), expanded from Bo Zhu's (http://about.bozhu.me)AES-128 implementation at https://github.com/bozhu/AES-Python
- AES-128, AES-192 and AES-256 implementations in pure python (very slow, butworks).Results have been tested against the NIST standard (http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf)
- CBC mode for AES with PKCS#7 padding (now also PCBC, CFB, OFB and CTR thanks to @righthandabacus!)
encryptanddecryptfunctions for protecting arbitrary data with apassword
RandomKeygen is a free mobile-friendly tool that offers randomly generated keys and passwords you can use to secure any application, service or device. KEY RandomKeygen - The Secure Password & Keygen Generator. DeveloperWorks blogs allow community members to share thoughts and expertise on topics that matter to them, and engage in conversations with each other. You can browse for and follow blogs, read recent entries, see what others are viewing or recommending, and request your own blog.
I want to generate AES encryption key to be sent to the the other party in order to communicate securely. In the beginning the two nodes will create a shared session key by using Deffie-Helman protocol, then one of them will genreate AES key and send it to the other node through the secure channel(i.e. DH protocol). Oct 05, 2016 The RNGCryptoServiceProvider class will generate random bytes in a fixed-length byte array. Cryptographic algorithms require keys of specific length such as 32-bit or 256-bit keys. Cryptographic algorithms require keys of specific length such as 32-bit or 256-bit keys.
Note: this implementation is not resistant to side channel attacks.
Although this is an exercise, the encrypt and decrypt functions shouldprovide reasonable security to encrypted messages. It ensures the data iskept secret (using AES), blocks are encrypted together (CBC), the samemessage encrypted twice will have different ciphertexts (salt), the ciphertexthasn't been tampered with (HMAC) and the key has some defense against brute-force(PBKDF2).
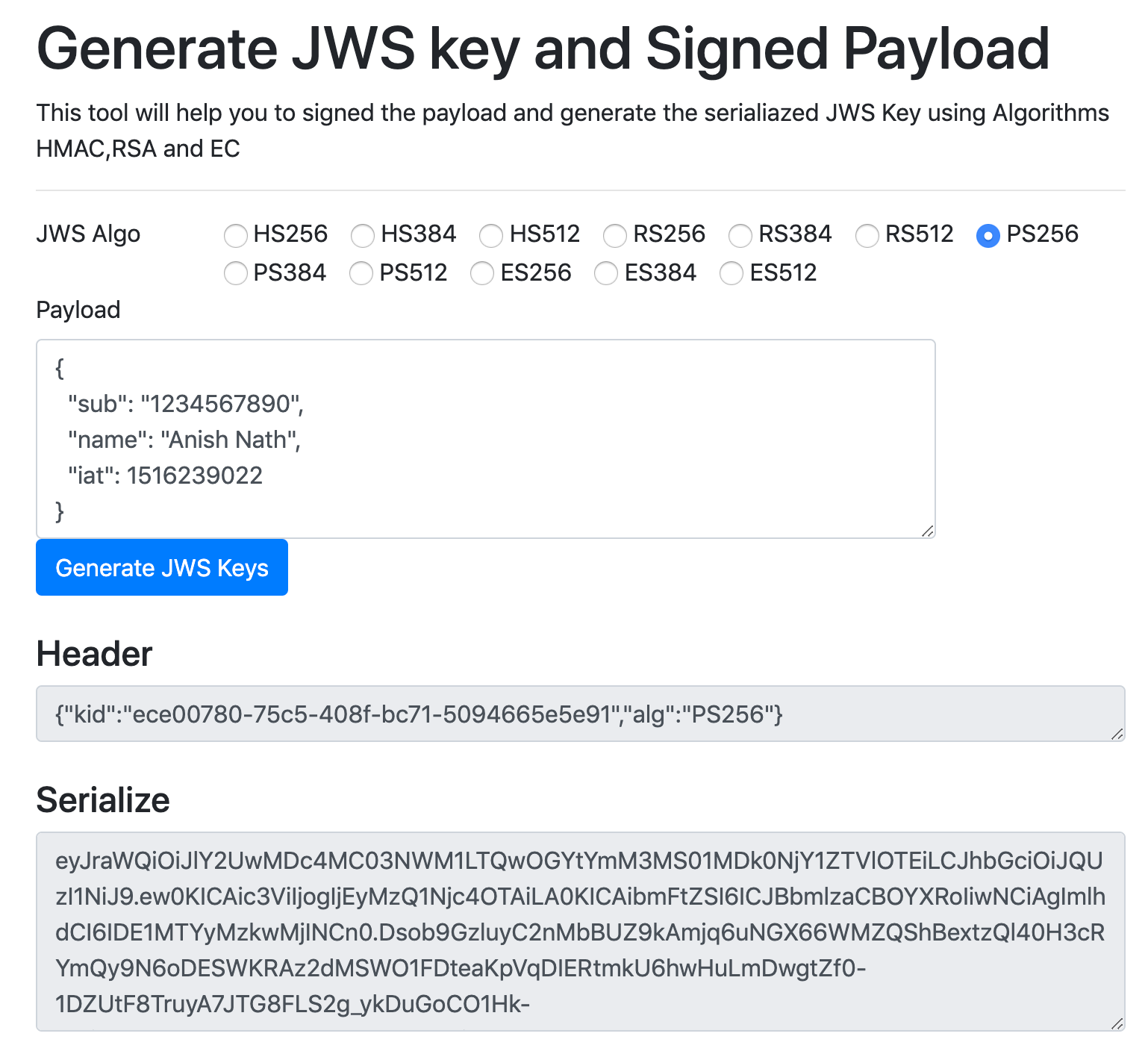
What Is 256 Bit
The algorithm is as follows:
16 random bytes of salt are extracted from the system's secure random numbergenerator (usually /dev/urandom)>
The given master key is stretched and expanded by PKBDF2-HMAC(SHA256) usingthe salt from 1), to generate the AES key, HMAC key and IV (initializationvector for CBC).
The given message is encrypted with AES-128 using the AES key and IV fromstep 2), in CBC mode and PKCS#7 padding.
A HMAC-SHA256 is generated from the concatenation of the salt from 1) andthe ciphertext from 3).
The final ciphertext is HMAC + salt + ciphertext.
256 Bit Color
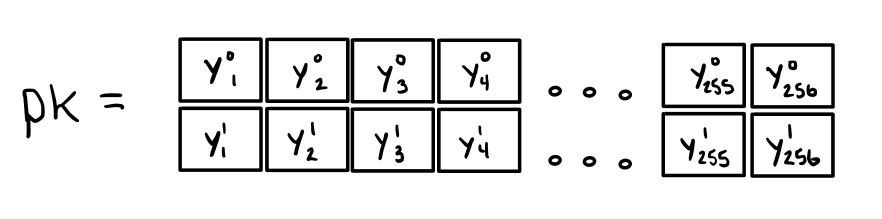
Subkey Generation For 256 Bit Key
Eset nod32 licence key free download. Security overview:
The random salt ensures the same message will map to different ciphertexts.
Dr fone key generator mac download. Transfer contacts, text messages, photos, videos, music and many other file types. Simple, click-through, process. Move data between devices with different operating systems, i.e iOS to Android. Compatible with the latest iOS 11 and Android 8.0.Wondershare Dr.Fone Switch Registration Code Crack + Free Activation#1.
The HMAC ensures the integrity of both the entire ciphertext and the PKBDF2salt; encrypt-then-mac prevents attacks like Padding Oracle.
Bytes from keys, iv and salt are not reused in different algorithms.
PBKDF2 key stretching allows for relatively weak passwords to be used as AESkeys and be moderately resistant to brute-force, but sacrificing performance.